Blosxom4Nagios
A little whole ago at one of my client sites we decided that we wanted to monitor the bulk of our Nagios notifications via RSS rather than via email or jabber. The centralised river-of-news architecture of RSS is just a much better fit for high-volume notification flow than the individual silos and persistent messaging nature of email.
There are a few nice RSS solutions out there for Nagios, including the following:
- S Sugar's RSS Notifications
- Steve Shipway's Nagios RSS
- Altinity's RSS4NAGIOS
We quite liked Altinity's RSS4NAGIOS because it was notifications (rather than alerts) based, and because it was pretty easy to just drop in and use. The only thing we didn't really like was that it was still relatively static - it provides nice per-user feeds, but you can't carve those feeds up or drill down to subsets of the data very easily. We wanted to be able to slice-and-dice things a bit more dynamically - be able to look at feeds for per-host, per-hostgroup, per-status, or date-filtered notifications, for example.
I'm also a blosxom developer, so I quickly realised that I could do everything I wanted pretty trivially using blosxom. All I needed was a script to capture and tag notifications as blosxom posts, and then I could have dynamic filtering, multi-dimensional tag-based feeds, etc., all pretty much for free.
So a couple of afternoons later, Blosxom4Nagios was up and running. It's basically a single-purpose blosxom install that you drop into a directory somewhere (/var/log/nagios/blosxom, by default), hook into apache for display, hook into nagios to accept notifications, and away you go.
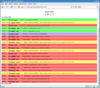
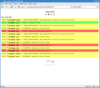
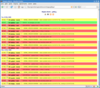
Notifications are tagged by type (host/service), state (OK, WARNING, CRITICAL etc.), hostname, hostgroup, service name, service group, contact, and date, so you can filter notifications based on any of these, and produce feeds (both RSS2 and atom) on any of them as well e.g.
- http://www.example.com/nagios/blosxom/tags/nagiosadmin
- http://www.example.com/nagios/blosxom/tags/hostgroup1/rss
- http://www.example.com/nagios/blosxom/tags/myhost/atom
- http://www.example.com/nagios/blosxom/tags/servicegroup2
- http://www.example.com/nagios/blosxom/tags/randomservice
- http://www.example.com/nagios/blosxom/tags/CRITICAL/atom
- http://www.example.com/nagios/blosxom/2008/03/tags/nagiosadmin
- http://www.example.com/nagios/blosxom/2008/03/19/tags/myhost/rss
etc.
Screenshots:
Blosxom4Nagios is available here:
and is licensed under the same MIT Licence as blosxom itself.
Comments and feedback welcome.